Integrating Jumio Services
Jumio provides services![]() An identity verification service provided by Jumio that evaluates a set of credentials and renders a decision. A service is invoked by a workflow. A workflow can invoke a single service or a sequence of services and/or risk signals. you use to verify and validate the individuals your business interacts with online. When an end user
An identity verification service provided by Jumio that evaluates a set of credentials and renders a decision. A service is invoked by a workflow. A workflow can invoke a single service or a sequence of services and/or risk signals. you use to verify and validate the individuals your business interacts with online. When an end user![]() A person who is a customer, patient, constituent, or client of a Jumio customer, and who participates in the “customer journey” as part of their interaction with the Jumio customer. is using your website or mobile app to do something that could potentially be fraudulent, you can pass that person’s credentials
A person who is a customer, patient, constituent, or client of a Jumio customer, and who participates in the “customer journey” as part of their interaction with the Jumio customer. is using your website or mobile app to do something that could potentially be fraudulent, you can pass that person’s credentials![]() A form of identification that is associated with an account. Jumio currently supports these types of credentials:
Government ID; Selfie; Facemap; Document; Data, which can be either Prepared Data or Device Data. to Jumio to determine the risk to your organization.
A form of identification that is associated with an account. Jumio currently supports these types of credentials:
Government ID; Selfie; Facemap; Document; Data, which can be either Prepared Data or Device Data. to Jumio to determine the risk to your organization.
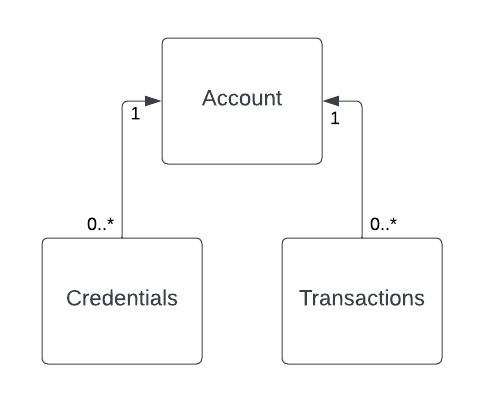
Accounts, Credentials, and Transactions
When credentials are passed to Jumio, they are associated with an account![]() A grouping of credentials and transactions associated with an end user.. If this is a new user you are onboarding, you create a new account and associate the credentials with it. If you want Jumio to perform some checks on a known user, you associate the credentials with an existing account.
A grouping of credentials and transactions associated with an end user.. If this is a new user you are onboarding, you create a new account and associate the credentials with it. If you want Jumio to perform some checks on a known user, you associate the credentials with an existing account.
Each time Jumio checks a set of credentials against any of the available services it creates a transaction![]() An executed business process that is associated with an account. The transaction applies credentials for the account to a workflow and contains the decision rendered by the workflow. that is associated with the account that the credentials belong to.
An executed business process that is associated with an account. The transaction applies credentials for the account to a workflow and contains the decision rendered by the workflow. that is associated with the account that the credentials belong to.
Workflows, Services, and Capabilities
Each transaction executes a ![]() A low-level business process that implements all or part of a service or risk signal. Individual capabilities provide the reasons for determining the transaction decision. or sequence of capabilities. Each capability evaluates one or more credentials and renders a decision
A low-level business process that implements all or part of a service or risk signal. Individual capabilities provide the reasons for determining the transaction decision. or sequence of capabilities. Each capability evaluates one or more credentials and renders a decision![]() Each transaction renders a decision about the credentials that were evaluated. The decision includes one of the following values: PASSED; WARNING; REJECTED. It also includes a risk score. The value is based on the score. based on the likelihood of the credentials being fraudulent. The workflow renders an overall decision on the fraud risk based on all the intermediate decisions rendered by the capabilities. The decision may be one of:
Each transaction renders a decision about the credentials that were evaluated. The decision includes one of the following values: PASSED; WARNING; REJECTED. It also includes a risk score. The value is based on the score. based on the likelihood of the credentials being fraudulent. The workflow renders an overall decision on the fraud risk based on all the intermediate decisions rendered by the capabilities. The decision may be one of:
- PASSED
No fraud detected
- REJECTED
Clear indications of fraud
- WARNING
Jumio is unable to make a definitive judgment. Typically you will want to initiate further review of the transaction by an analyst.
Let’s explore how Jumio services may be used in the context of some common user interactions.
-
Global Identity Check Example describes how form data entered by an end user can be used to make a quick identity risk assessment.
-
Identification Card and Identity Verification Example describes a typical user onboarding interaction.
-
Authentication Example describes how a user can provide a selfie to verify that he or she is a known and trusted user.